Identifying Cyber Threats

 With so many vulnerabilities discovered daily and viruses released to exploit them, it’s easy to overlook a threat. This guide serves to help you identify common cyber threats in the wild today. Unfortunately, it takes only a single click to inadvertently infect your computer; anti-virus and anti-spam software isn’t always perfect, therefore education is key.
With so many vulnerabilities discovered daily and viruses released to exploit them, it’s easy to overlook a threat. This guide serves to help you identify common cyber threats in the wild today. Unfortunately, it takes only a single click to inadvertently infect your computer; anti-virus and anti-spam software isn’t always perfect, therefore education is key.
Know that Macs and Smart Phones are NOT immune!
Phishing Attacks/Fake Emails
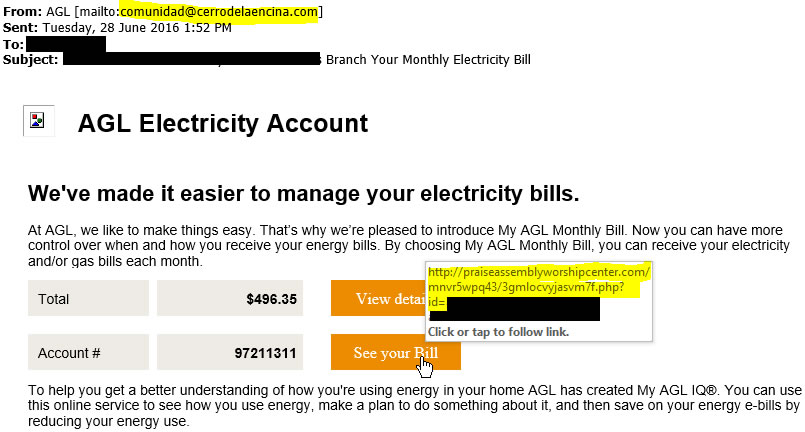
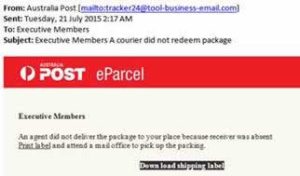 Quite often in the form of an email seemingly from a trusted provider (e.g. Bank, Australia Post, ATO, Apple iTunes or even a Photocopier). These emails either include a malicious attachment or a link requesting your information.
Quite often in the form of an email seemingly from a trusted provider (e.g. Bank, Australia Post, ATO, Apple iTunes or even a Photocopier). These emails either include a malicious attachment or a link requesting your information.
In most cases, the easiest way to check the email’s legitimacy is to check the Sender’s email address. Although the name might appear legitimate, the actual address is rarely from the actual provider.
Phone Calls/Social Engineering
Australia has seen a rise of phone calls in recent years from those falsely claiming to be from Microsoft, Telstra and even the ATO. Requests range from demaning money for unpaid bills/taxes to claiming your computer has a virus and offering to remotely assist.
Always exercise caution when receiving calls from providers wanting information, demanding payment and wanting to gain remote access to your computer. Instead, ask for their name, a reference number and a phone number to call them back. These false providers will usually hang up upon requesting this information. If they do happen to provide details, do your research, Google the number to ensure it’s legitimacy. Don’t necessarily call the number back, call the provder’s main number instead and query the reference number.
Advertising
A very simple one… Websites filled with ads often making false claims or offering a free eBook, etc. While these ads may not directly infect your computer, they will usually ask for your email address in return for a free item or download. Once your email address has been captured, it is often sold to various companies and marketing agencies who will in turn begin sending spam emails to you.
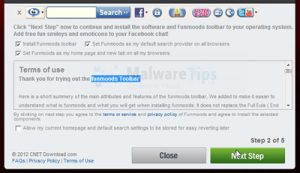 Bundled Software
Bundled Software
Many programs downloaded are often bundled with additional free software, even legitimate programs such as Java. These bundled programs (i.e. Toolbars, Search Apps, etc.) are usually unwanted.
Take care when installing any programs and be sure to read what you’re accepting. Check out this awesome little app to help avoid accidentally installing bundled software – Unchecky.
Malware/USB Drives
Malware comes in many forms however the most noteable of late is known as Ransomware. Infections are delivered via email, websites, and may even infect files on a USB drive which is then connected to other computers infecting those.
Always ensure your anti-virus software is up to date and regular full system scans are completed. Free Anti-Virus programs often lack more advanced detections features, though are better than nothing. Computers managed by Noytech under our Managed Services Agreement are fully protected, updated every few hours and complete a Full System Scan every week. Unfortunately, regardless of what Anti-Virus software is running on your computer, certain emails do still come through undetected so please don’t assume you’re protected against threats.
For more information and staying alert to new Scams and Cyber Threats: