Understanding Ransomware & Importance of Prevention
What is Ransomware?
You’re no doubt aware that ransomware attacks are increasing worldwide, including within Australia. But what is ransomware?
Ransomware is a type of virus or malicious software (malware) that will search for and encrypt/lock any files it can access including shared network drives and computers. This includes all your Word/Excel files, Photos, Music, Videos, Emails and more. Your files are held at ‘ransom’ as payment is demanded before you can regain access.
Depending on the type or variant of ransomware, as well as the level of permission you have on your computer, significant damage can be done to your computer requiring a complete wipe and rebuild.
While ransomware is the most common type of infection today, typical viruses still exist and should not be discounted.
How can I be infected?
Ransomware infections are typically introduced in one of two ways.
- Remote Access attacks – Attackers regularly use brute force attacks or otherwise to try to gain access to businesses with remote access enabled. Since remote access is widely used for WFH solutions, it becomes a considerable and easy target for attackers. Users with less secure passwords become an effortless target for access and ransomware infections to be planted.
>> Click here to find out how secure your Password is. - Phishing attacks – Attackers regularly send phishing (scam) emails that may appear legitimate directing users to click on malicious links or open infected attachments. Opening attachments and links from phishing emails or websites may allow the ransomware infection to run quickly and without further prompt.
>> Learn how to Identify a Cyber Threat
What are the repercussions?
Consider how much you and your business rely on Computer systems and all the data stored on them. Downtime may be anywhere from hours to weeks or longer depending on the severity of the infection. Consider staff downtime, loss of income, cost of wages and other expenses, inability to respond to Clients, potential breach and exposure of sensitive company data, the reputation of the business, insurance proceedings and potential data breach fines if not handled correctly.
All of these factors must be appreciated to understand why prevention is key.
How do I know if I’ve been infected?
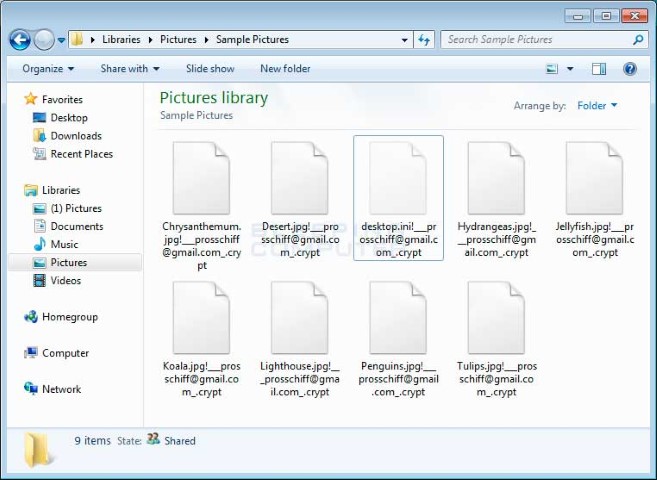
A ransomware infection will generally prompt the user quite quickly with a warning screen advising that files have been locked and must process payment to unlock them. Further, you may notice that files have been renamed and the icon changes or disappears.
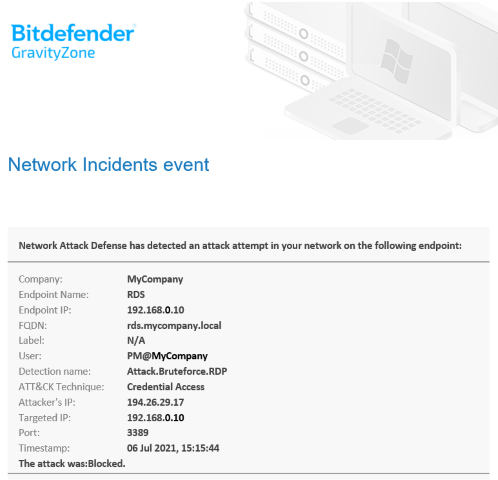
Security Alert of blocked Remote Attack
What protections are in place?
NOYTECH employs numerous Security Standards outlined in the ‘Security Policy’ document available upon request. These standards outline the level of permission Users have on their Computers, the Security software in place to prevent and block Brute Force Remote Access Attacks, as well as recommendations around the use of 2-Factor Authentication (2FA) where applicable. While Anti-Virus Software is utilised and Email Systems typically include anti-spam & anti-malware filtering, there is always a chance that a virus can be introduced.
Please refer to the NOYTECH Security Policy for more information.
What can I do to protect myself?
There are several services readily available to help Users identify whether their email address and password have already been exposed, or, are exposed in a future breach.
- https://haveibeenpwned.com/ – Enter your email address on this site and learn of any existing data breaches containing your email address. You can also signup to be notified of future breaches.
- Firefox/Chrome built-in Password Managers now check whether saved passwords have been compromised. To view compromised passwords, open your Browser Settings > Passwords and look for the relevant section.
- Change your passwords immediately. Especially any of those that have been compromised or you know are weak. It’s advised to use a different password for your top-level email account itself to limit the number of other services breached with just one exposed email address and password. g. My littlejonny@gmail.com Email Account password is Smart@rse.00, however, my login for PayPal is littlejonny@gmail.com with a password SmartMoney.888.
- Enable 2-Factor Authentication (2FA) on everything, especially those top-level email accounts used for other services. Like Internet Banking, 2FA adds an extra layer of protection to your accounts. Therefore, even if your email address and password are exposed online, an attacker is unable to access the account without the extra code delivered to your phone. Most services will allow you to ‘remember login’ on a trusted computer/device meaning you don’t have to enter a 2FA code every time. While 2FA prompts can be an inconvenience at times, the alternative is significantly worse.
- Backup, backup, backup! – As always, the recommendation is to NEVER pay the ransom. However, unless a protected backup is available to restore encrypted files, there may not be a way to retrieve files. A ‘protected backup’ is not connected to the computer/network when at rest.
It’s important to understand that ransomware is not restricted to only Windows computers. Mac and mobile devices are susceptible therefore all precautions must be taken to properly prevent infection or at least minimise the damage caused.